Ransomware attacks—malware intrusions that block an organization’s access to its own data until a ransom is paid—are taking on alarming new aspects. As people’s work habits, daily routines, geographic locations, and trust in institutions have changed against a backdrop of global political shifts and the covid-19 pandemic, ransomware attacks have taken advantage of the opportunity to grow more sophisticated and pervasive.

Though the basic tools of ransomware remain the same, attackers are using global uncertainty as cover to evolve techniques that make extortion attempts more effective. In a “double extortion” attack, for example, bad actors both block the organization’s access to data and threaten to release or sell that data.
“Triple extortion” or “quadruple extortion” attacks, which additionally incorporate distributed denial of service (DDoS) attacks or threats to third parties, are now also part of the modern risk landscape, according to Alexander Applegate of cybersecurity firm ZeroFox.
Meanwhile, attempted attacks have also grown so prevalent as to be virtually guaranteed. According to a 2022 Sophos survey, 66% of companies experienced a ransomware attack in the last year, nearly double the 2020 figure. A 2022 report by Enterprise Strategy Group (ESG) put the figure at 79% of organizations affected in the last year.
ESG practice director and senior analyst Christophe Bertrand inserts this troubling addition: “I question the 21% who say they did not experience an attack, because I think the ransomware virus is probably dormant in their systems.”
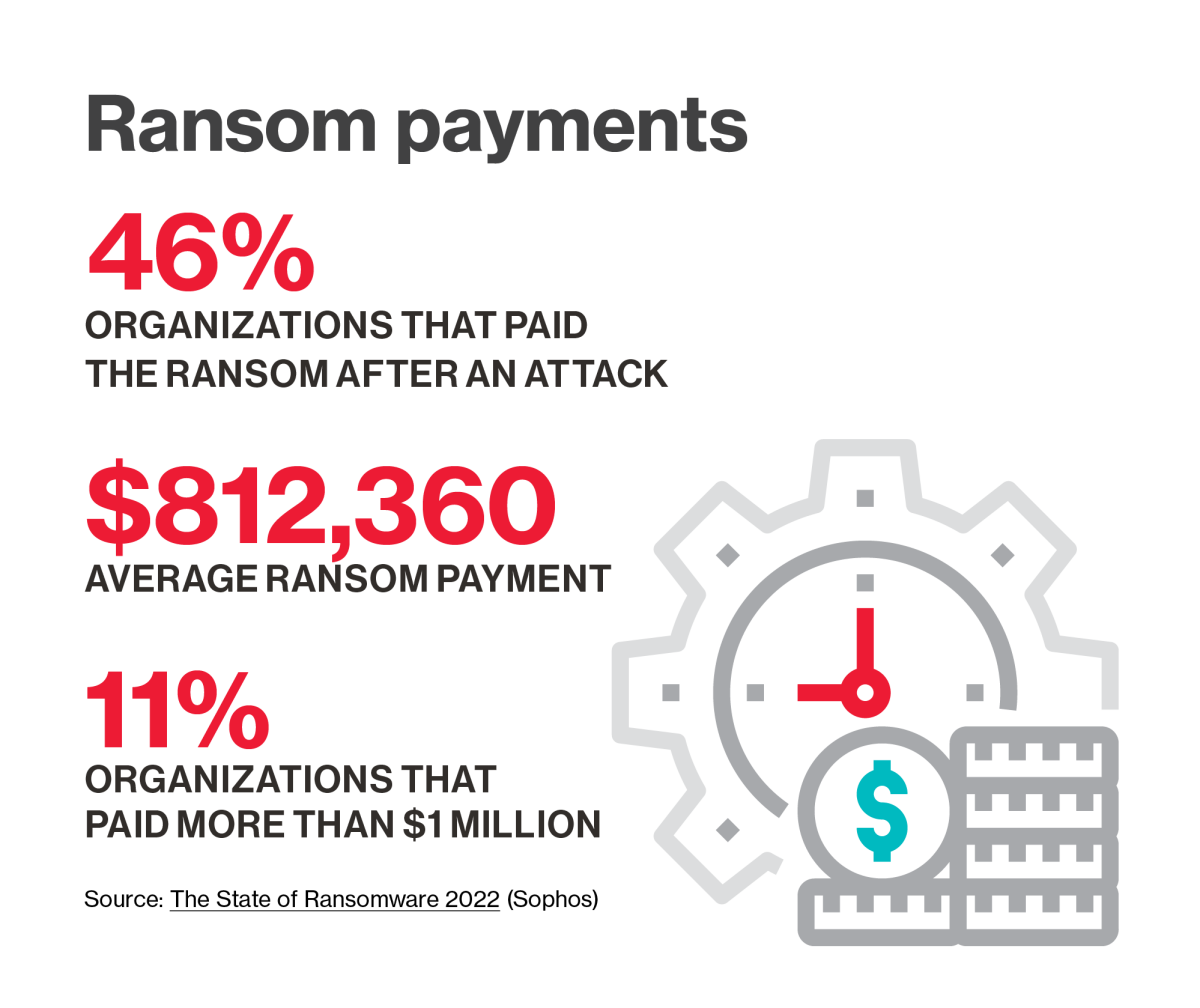
Ransomware attacks have grown more virulent
Ransomware threats have become more damaging in several dimensions: attacks are on the rise, cybercriminals are demanding more ransom, successful intrusions are being leveraged to compromise multiple data streams, and attacks are spreading beyond IT systems into critical infrastructure essential to business functioning.
A 2022 Sophos report identified a new trend: a franchise business model (“ransomware-as-a-service”) in which gangs sell ransomware kits to other cybercriminals, who launch the attacks and then return a portion of the proceeds back to the gang. “When ransomware started, it was a small business picking on users who weren’t sophisticated and who would probably pay a couple of hundred dollars to get their data back,” says Hu Yoshida, chief technology officer at Hitachi Vantara. “But now the game has changed dramatically.”
The utility industry has become an enticing target, as disrupting power, water, or critical infrastructure can be detrimental to the public. The 2021 ransomware attack against Colonial Pipeline, for example, spurred gas shortages in the northeastern United States. And though Colonial Pipeline paid the $4.4 million ransom, the decryption tool provided by the hackers was so ineffective that the company ended up using its own business continuity systems to slowly get back up and running.

Governments and public services also have become ransomware targets. A U.S. Senate committee report noted more than 2300 known ransomware attacks on local governments, schools, and healthcare providers in the U.S. in 2021. In April and May 2022, a series of ransomware attacks crippled dozens of Costa Rican government agencies, including the Ministry of Finance and the social security system, spurring the president to declare a national emergency.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review’s editorial staff.




Post a Comment